Mar 26, 2011
Corruption In India Funny Video..Quit True..
Corruption In India: A Billion Dollar Industry
Political corruption and bureaucratic corruption in India are major concerns. A 2005 study done by Transparency International in India found that more than 15% of the people in India had firsthand experience of paying bribe or peddling influence to get any type of job done in a public office. Taxes and bribes are a daily life fact, common between state borders; Transparency International estimates that truckers pay annually US$5 billion in bribes.For 2010, India was ranked 87th of 178 countries in Transparency International's Corruption Perceptions Index. As of 2010, India is the ninth-most corrupt country in the world, with about 54% of Indians paying a bribe in the past year, according to a global survey by Transparency International (TI). India needs to deal with the malice of corruption and improve governance in Asia's third-largest economy, Prime Minister Manmohan Singh said on 18 March 2011.Recently, due to international pressure, the Swiss government agreed to disclose the names of the account holders only if the respective governments formally asked for it.. Indian government is not asking for the details….. ..no marks for guessing why?
We need to start a movement to pressurise the government to do so! This is perhaps the only way, and a golden opportunity, to expose the high and mighty and weed out corruption!
Please read on……and forward to all the honest Indians to…..like somebody is forwarding to you…….and build a ground-swell of support for action ! Is India poor, who says? Ask the Swiss banks. With personal account deposit bank of $1,500 billion in foreign reserve which have been misappropriated, an amount 13 times larger than the country’s foreign debt, one needs to rethink if India is a poor country?
DISHONEST INDUSTRIALISTS, scandalous politicians and corrupt IAS, IRS, IPS officers have deposited in foreign banks in their illegal personal accounts a sum of about $1500 billion, which have been misappropriated by them. This amount is about 13 times larger than the country’s foreign debt. With this amount 45 crore poor people can get Rs 1,00,000 each.
Do comment Please...
Mar 18, 2011
LINUX

Linux (commonly /ˈlɪnəks/ LIN-əks in English, also pronounced /ˈlɪnʊks/ LIN-ooks in Europe) refers to the family ofUnix-like computer operating systems using the Linux kernel. Linux can be installed on a wide variety of computer hardware, ranging from mobile phones, tablet computers and video game consoles, to mainframes and supercomputers.Linux is a leading server operating system, and runs the 10 fastest supercomputers in the world.
The development of Linux is one of the most prominent examples of free and open source software collaboration; typically all the underlying source code can be used, freely modified, and redistributed, both commercially and non-commercially, by anyone under licenses such as the GNU General Public License. Typically Linux is packaged in a format known as a Linux distribution for desktop and server use. Some popular mainstream Linux distributions include Debian (and its derivatives such as Ubuntu), Fedora and openSUSE. Linux distributions include the Linux kernel and supporting utilities and libraries to fulfill the distribution's intended use.
A distribution oriented toward desktop use may include the X Window System, the GNOME and KDE Plasma desktop environments. Other distributions may include a less resource intensive desktop such as LXDE or Xfce for use on older or less-powerful computers. A distribution intended to run as a server may omit any graphical environment from the standard install and instead include other software such as the Apache HTTP Server and a SSH server like OpenSSH. Because Linux is freely redistributable, it is possible for anyone to create a distribution for any intended use. Commonly used applications with desktop Linux systems include the Mozilla Firefox web-browser, the OpenOffice.org office application suite and the GIMPimage editor.
The name "Linux" comes from the Linux kernel, originally written in 1991 by Linus Torvalds. The main supporting user spacesystem tools and libraries from the GNU Project (announced in 1983 by Richard Stallman) are the basis for the Free Software Foundation's preferred name GNU/Linux.


Feb 8, 2011
Lets Google "GOOGLE"..
Google began in March 1996 as a research project by Larry Page and Sergey Brin, Ph.D. students at Stanford working on the Stanford Digital Library Project (SDLP). The SDLP's goal was “to develop the enabling technologies for a single, integrated and universal digital library." and was funded through the National Science Foundation among other federal agencies. In search for a dissertation theme, Page considered—among other things—exploring the mathematical properties of the World Wide Web, understanding its link structure as a huge graph. His supervisor Terry Winograd encouraged him to pick this idea (which Page later recalled as "the best advice I ever got") and Page focused on the problem of finding out which web pages link to a given page, considering the number and nature of such backlinks to be valuable information about that page (with the role of citations in academic publishing in mind). In his research project, nicknamed "BackRub", he was soon joined by Sergey Brin, a fellow Stanford Ph.D. student supported by a National Science Foundation Graduate Fellowship. Brin was already a close friend, whom Page had first met in the summer of 1995 in a group of potential new students which Brin had volunteered to show around the campus. Page's web crawler began exploring the web in March 1996, setting out from Page's own Stanford home page as its only starting point. To convert the backlink data that it gathered into a measure of importance for a given web page, Brin and Page developed the PageRank algorithm.Analyzing BackRub's output—which, for a given URL, consisted of a list of backlinks ranked by importance—it occurred to them that a search engine based on PageRank would produce better results than existing techniques (existing search engines at the time essentially ranked results according to how many times the search term appeared on a page).
A small search engine called "RankDex" from IDD Information Services (a subsidiary of Dow Jones designed by Robin Li was, since 1996, already exploring a similar strategy for site-scoring and page ranking. The technology in RankDex would be patented and used later when Li founded Baidu in China.
Convinced that the pages with the most links to them from other highly relevant Web pages must be the most relevant pages associated with the search, Page and Brin tested their thesis as part of their studies, and laid the foundation for their search engine. By early 1997, the backrub page described the state as follows:
A small search engine called "RankDex" from IDD Information Services (a subsidiary of Dow Jones designed by Robin Li was, since 1996, already exploring a similar strategy for site-scoring and page ranking. The technology in RankDex would be patented and used later when Li founded Baidu in China.
Convinced that the pages with the most links to them from other highly relevant Web pages must be the most relevant pages associated with the search, Page and Brin tested their thesis as part of their studies, and laid the foundation for their search engine. By early 1997, the backrub page described the state as follows:
Some Rough Statistics (from August 29th, 1996)
Total indexable HTML urls: 75.2306 Million
Total content downloaded: 207.022 gigabytes
...
BackRub is written in Java and Python and runs on several Sun Ultras and Intel Pentiums running Linux. The primary database is kept on an Sun Ultra II with 28GB of disk. Scott Hassan and Alan Steremberg have provided a great deal of very talented implementation help. Sergey Brin has also been very involved and deserves many thanks.
-Larry Page page@cs.stanford.edu
Feb 2, 2011
Song tune mere jana kabhi nahi jana ishq mera dard mera .. Ho love of mine

Ho love of mine..
with a song and a whine..
You’re harsh and divine..
like truths and a lie..
but the tale end is not here..
I’ve nothing to fear..
for my love is yell of giving and hold on…
in the bright emptiness..
in a room full of it..
is the cruel mistress ho ho o…
I feel the sunrise..
that nest all hollowness..
for i have the way to go.. not come…
And i feel so lonely yea..
There’s a better place from this emptiness..
And i’m so lonely yea..
There’s a better please from this emptiness.. yei yei yei ya….
Aa.. aa.. aa…..
Tune mere jaana..
Kabhi nahi jana..
Ishq mera dard mera.. haaye…
Tune mere jaana..
Kabhi nahi jana..
Ishq mera dard mera …
Aashiq teraaa..
Bheed mein khoya rehta hai..
Jaane jahaan a..
Puchho toh itna kehta hai..
And i feel so lonely yea..
There’s a better place from this emptiness..
And i’m so lonely yea..
There’s a better please from this emptiness.. yei yei yei ya….
Click Here To Download
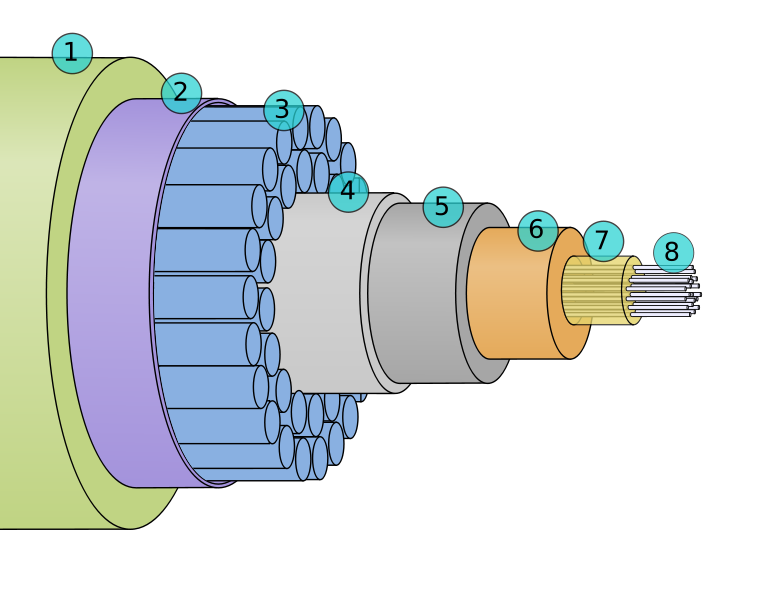
Submarine communications cable

Click for large image
A submarine communications cable is a cable laid beneath the sea to carry telecommunications under stretches of water.

The first submarine communications cables carried telegraphy traffic. Subsequent generations of cables carried first telephony traffic, then data communications traffic. All modern cables use optical fiber technology to carry digital payloads, which are then used to carry telephone traffic as well as Internet and private data traffic. They are typically 69 millimetres (2.7 in) in diameter and weigh around 10 kilograms per metre (7 lb/ft), although thinner and lighter cables are used for deep-water sections.

Feb 1, 2011
Intel Adds New Members In Its Processor Family

Intel introduced the second generation Intel Core processor family. Throughout the next year, more than 500 desktops and laptops are expected from all major OEMs worldwide. In India, systems are likely to be available from OEMs like HCL, Wipro, MSI, HP, Lenovo, Toshiba and Dell amongst others as well as from local channel partners.
The processor features include, Intel quick sync video, and a new version of Intel Wireless Display (WiDi), which now adds 1080p HD and content protection for those wishing to beam premium HD content from their laptop screen to their TV. “The new second generation Intel Core processors represent the biggest advance in computing performance and capabilities over any other previous generation,” said R Sivakumar, Managing Director, Sales and Marketing Group, Intel South Asia.
The second generation Intel Core processor family is the first micro architecture to combine visual and 3D graphics technology with performance-leading microprocessors on a single chip. Incorporating the newly architected Intel HD graphics on each 32nm die enables significant graphics performance improvements over previous generation graphics, for both HD media processing and mainstream gaming.
The new processor graphics technology will focus on high-definition (HD) video, photos, mainstream gaming, multi-tasking and online socializing and multimedia.
“Today, the consumption patterns clearly indicate a shift towards heavy access to online audio and video content by mainstream users and I am confident our partnership will produce a range of products that will address the growing need, offering mainstream users an immersive computing experience on our products powered by the 2nd generation Intel Core processors,” said George Paul, Executive Vice President, HCL Infosystems.
“The second generation Core processor family promises to offer a better set of visual capabilities that’s now seamlessly integrated with the processor performance. We’re very excited to bring to market a set of products based on these new processors, which will offer the consumers an unparalleled and entertaining PC experience,” added Amar Babu, Managing Director, Lenovo India.
sourse-www.crn.in
Waht is 3G..

3G is the third generation of wireless technologies. It comes with enhancements over previous wireless technologies, like high-speed transmission, advanced multimedia access and global roaming. 3G is mostly used with mobile phones and handsets as a means to connect the phone to the Internet or other IP networks in order to make voice and video calls, to download and upload data and to surf the net.
3G has the following enhancements over 2.5G and previous networks:
- Several times higher data speed;
- Enhanced audio and video streaming;
- Video-conferencing support;
- Web and WAP browsing at higher speeds;
- IPTV (TV through the Internet) support.
3G Technical Specifications:
The transfer rate for 3G networks is between 128 and 144 kbps (kilobits per second) for devices that are moving fast and 384 kbps for slow ones(like for pedestrians). For fixed wireless LANs, the speed goes beyond 2 Mbps. 3G is a set of technologies and standards that include W-CDMA, WLAN and cellular radio, among others.
3G follows a pattern of G's that started in the early 1990's by the ITU. The pattern is actually a wireless initiative called the IMT-2000 (International Mobile Communications 2000). 3G therefore comes just after 2G and 2.5G, the second generation technologies. 2G technologies include, among others, the Global System for Mobile (GSM) - the famous mobile phone technology we use today. 2.5G brings standards that are midway between 2G and 3G, including the General Packet Radio Service (GPRS), Enhanced Data rates for GSM Evolution (EDGE), Universal Mobile Telecommunications System (UMTS) etc.
What is Required for Using 3G?:
The first thing you require is a device (e.g. a mobile phone) that is 3G compatible. This is where the name 3G phone comes from - a phone that has 3G functionality; nothing to do with the number of cameras or the memory it has. An example is the iPhone 3G. 3G phones commonly have two cameras since the technology allows the user to have video calls, for which a user-facing camera is required for capturing him/her.
Unlike with Wi-Fi which you can get for free in hotspots, you need to be subscribed to a service provider to get 3G network connectivity. We often call this kind of service a data plan or network plan.
Unlike with Wi-Fi which you can get for free in hotspots, you need to be subscribed to a service provider to get 3G network connectivity. We often call this kind of service a data plan or network plan.
Your device is connected to the 3G network through its SIM card (in the case of a mobile phone) or its 3G data card (which can be of different types: USB, PCMCIA etc.), which are both generally provided/sold by the service provider. Through that, you get connected to the Internet whenever you are within a 3G network. Even if you are not in one, you can still use 2G or 2.5G services provided by the service provider.
What Does 3G Cost?:
3G is not very cheap, but it is worthwhile for users that need connectivity on the move. Some providers offer it within a somewhat costly package, but most of them have plans where the user pays for the amount of data transferred. This is because the technology is packet-based. For example, there are service plans where there is a flat rate for the first Gigabyte of data transferred, and a per minute cost for each additional Megabyte.
3G and Voice:
Wireless technologies are a way for mobile users to make free or cheap calls worldwide and save a lot of money due to the latest telephony applications and services. 3G networks have the advantage of being available on the move, unlike Wi-Fi, which is limited to a few meters around the emitting router. So, a user with a 3G phone and a 3G data plan is well-equipped for making free mobile calls. She will only have to download one of the free applications and install on her mobile phone and start making calls.*sourse:=voip.about.com
BRAIN VIRUS

©Brain affects the IBM PC computer by replacing the boot sector of a floppy disk with a copy of the virus. The real boot sector is moved to another sector and marked as bad. Infected disks usually have five kilobytes of bad sectors. The disk label is changed to ©Brain, and the following text can be seen in infected boot sectors:
- Welcome to the Dungeon © 1986 Brain & Amjads (pvt) Ltd VIRUS_SHOE RECORD V9.0 Dedicated to the dynamic memories of millions of viruses who are no longer with us today - Thanks GOODNESS!! BEWARE OF THE er..VIRUS : this program is catching program follows after these messages....$#@%$@!!
There are many minor and major variations to that version of the text. The virus slows down the floppy disk drive and makes seven kilobytes of memory unavailable to DOS. ©Brain was written by two brothers, Basit and Amjad Farooq Alvi, who lived in Chahmiran near Lahore Railway Station, Lahore, Pakistan. The brothers told TIME magazine they had written it to protect their medical software from piracy and it was supposed to target copyright infringers only. The cryptic message "Welcome to the Dungeon", appeared after a year because the brothers licensed a beta version of the code, a safeguard and reference to an early programming forum on Dungeon BBS. The brothers could not be contacted to receive the final release of this version of the program.

©Brain lacks code for dealing with hard disk partitioning, and avoids infecting hard disks by checking the most significant bit of the BIOS drive number being accessed; ©Brain does not infect the disk if the bit is clear, unlike other viruses at the time which paid no attention to disk partitioning and consequentially destroyed data stored on hard disks by treating them in the same way as floppy disks. ©Brain often went undetected partially due to this deliberate non-destructiveness, especially when the user paid little to no attention to the slow speed of floppy disk access.
The virus came complete with the brothers' address and three phone numbers, and a message that told the user that their machine was infected and for inoculation the user should call them:
- Welcome to the Dungeon © 1986 Basit * Amjad (pvt) Ltd. BRAIN COMPUTER SERVICES 730 NIZAM BLOCK ALLAMA IQBAL TOWN LAHORE-PAKISTAN PHONE: 430791,443248,280530. Beware of this VIRUS.... Contact us for vaccination...
The reason for this message was the program was originally used to track a heart monitoring program for the IBM PC, and pirates were distributing bad copies of the disks. This tracking program was supposed to stop and track illegal copies of the disk. Another programmer copied the technique for DOS and it became the (c) Brain virus. Unfortunately the program also sometimes used the last 5k on an apple floppy, making additional saves to the disk by other programs impossible. The company was sued for damages and was quickly dissolved.












